You may have read at NYMag that I’ve been in discussions with the Clinton campaign about whether it might wish to seek recounts in critical states. Thatarticle, which includes somebody else’s description of my views, incorrectly describes the reasons manually checking ballots is an essential security safeguard (and includes some incorrect numbers, to boot). Let me set the record straight about what I and other leading election security experts have actually been saying to the campaign and everyone else who’s willing to listen.
How might a foreign government hack America’s voting machines to change the outcome of a presidential election? Here’s one possible scenario. First, the attackers would probe election offices well in advance in order to find ways to break into their computers. Closer to the election, when it was clear from polling data which states would have close electoral margins, the attackers might spread malware into voting machines in some of these states, rigging the machines to shift a few percent of the vote to favor their desired candidate. This malware would likely be designed to remain inactive during pre-election tests, do its dirty business during the election, then erase itself when the polls close. A skilled attacker’s work might leave no visible signs — though the country might be surprised when results in several close states were off from pre-election polls.
Could anyone be brazen enough to try such an attack? A few years ago, I might have said that sounds like science fiction, but 2016 has seen unprecedented cyberattacks aimed at interfering with the election. This summer, attackers broke into the email system of the Democratic National Committee and, separately, into the email account of John Podesta, Hillary Clinton’s campaign chairman, and leaked private messages. Attackers infiltrated the voter registration systems of two states, Illinois and Arizona, and stole voter data. And there’s evidence that hackers attempted to breach election offices in several other states.
In all these cases, Federal agencies publicly asserted that senior officials in the Russian government commissioned these attacks. Russia has sophisticated cyber-offensive capabilities, and has shown a willingness to use them to hack elections. In 2014, during the presidential election in Ukraine, attackers linked to Russia sabotaged the country’s vote-counting infrastructure and, according to published reports, Ukrainian officials succeeded only at the last minute in defusing vote-stealing malware that was primed to cause the wrong winner to be announced. Russia is not the only country with the ability to pull off such an attack on American systems — most of the world’s military powers now have sophisticated cyberwarfare capabilities.
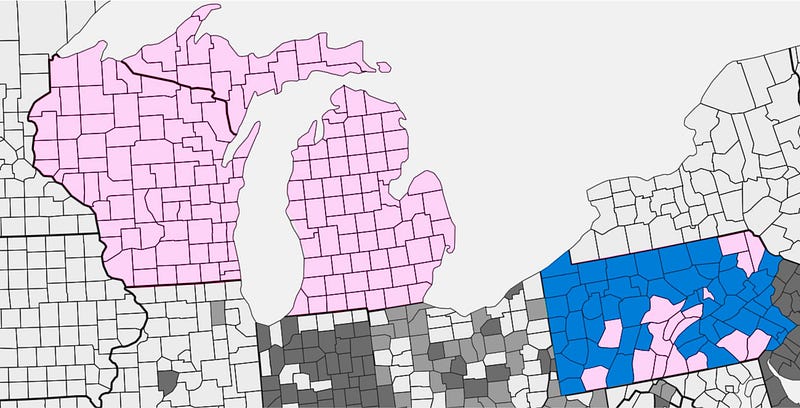
The pink counties predominately use optical scan paper ballots, which can be examined to confirm that the computer voting machines produced an accurate count. Blue counties use paperless voting systems, which require forensic analysis.
Were this year’s deviations from pre-election polls the results of a cyberattack? Probably not. I believe the most likely explanation is that the polls were systematically wrong, rather than that the election was hacked. But I don’t believe that either one of these seemingly unlikely explanations is overwhelmingly more likely than the other. The only way to know whether a cyberattack changed the result is to closely examine the available physical evidence — paper ballots and voting equipment in critical states like Wisconsin, Michigan, and Pennsylvania. Unfortunately, nobody is ever going to examine that evidence unless candidates in those states act now, in the next several days, to petition for recounts.
What’s to stop an attack like this from succeeding?
America’s voting machines have serious cybersecurity problems. That isn’t news. It’s been documented beyond any doubt over the last decade innumerous peer-reviewed papers and state-sponsored studies by me and by other computer security experts. We’ve been pointing out for years that voting machines are computers, and they have reprogrammable software, so if attackers can modify that software by infecting the machines with malware, they can cause the machines to give any answer whatsoever. I’ve demonstrated this in the laboratory with real voting machines — in just a few seconds, anyone can install vote-stealing malware on those machines that silently alters the electronic records of every vote.
It doesn’t matter whether the voting machines are connected to the Internet. Shortly before each election, poll workers copy the ballot design from a regular desktop computer in a government office, and use removable media (like the memory card from a digital camera) to load the ballot onto each machine. That initial computer is almost certainly not well secured, and if an attacker infects it, vote-stealing malware can hitch a ride to every voting machine in the area. There’s no question that this is possible for technically sophisticated attackers. (If my Ph.D. students and I were criminals, I’m sure we could pull it off.) If anyone reasonably skilled is sufficiently motivated and willing to face the risk of getting caught, it’s happened already.
Why hasn’t more been done about this? In the U.S., each state (and often individual counties or municipalities) selects its own election technology, and some states have taken steps to guard against these problems. (For instance, California banned the use of the most dangerous computer voting machinesin 2007 as a result of vulnerabilities that I and other computer scientists found.) But many states continue to use machines that are known to be insecure — sometimes with software that is a decade or more out of date — because they simply don’t have the money to replace those machines.
There is one absolutely essential security safeguard that protects most Americans’ votes: paper.
I know I may sound like a Luddite for saying so, but most election security experts are with me on this: paper ballots are the best available technology for casting votes. We use two main kinds of paper systems in different parts of the U.S. Either voters fill out a ballot paper that gets scanned into a computer for counting (optical scan voting), or they vote on a computer that counts the vote and prints a record on a piece of paper (called a voter-verifiable paper audit trail). Either way, the paper creates a record of the vote that can’t be later modified by any bugs, misconfiguration, or malicious software that might have infected the machines.
After the election, human beings can examine the paper to make sure the results from the voting machines accurately determined who won. Just as you want the brakes in your car to keep working even if the car’s computer goes haywire, accurate vote counts must remain available even if the machines are malfunctioning or attacked. In both cases, common sense tells us we need some kind of physical backup system. I and other election security experts have been advocating for paper ballots for years, and today, about 70% of American voters live in jurisdictions that keep a paper record of every vote.
Washington Journal: J. Alex Halderman on Cybersecurity and Voting
Oct. 4, 2016: Prof. J. Alex Halderman, who has conducted research on voting machine security, talks about his concerns regarding the nation’s voting systems.www.c-span.org
There’s just one problem, and it might come as a surprise even to many security experts: no state is planning to actually check the paper in a way that would reliably detect that the computer-based outcome was wrong. About half the states have no laws that require a manual examination of paper ballots, and most other states perform only superficial spot checks. If nobody looks at the paper, it might as well not be there. A clever attacker would exploit this.
There’s still one way that some of this year’s paper ballots could be examined. In many states, candidates can petition for a recount. The candidate needs to pay the cost, which can run into millions of dollars. The deadlines for filing recount petitions are soon — for example, this Friday in Wisconsin (margin 0.7%), Monday in Pennsylvania (margin 1.2%), and the following Wednesday in Michigan (margin 0.3%).
Examining the physical evidence in these states — even if it finds nothing amiss — will help allay doubt and give voters justified confidence that the results are accurate. It will also set a precedent for routinely examining paper ballots, which will provide an important deterrent against cyberattacks on future elections. Recounting the ballots now can only lead to strengthened electoral integrity, but the window for candidates to act is closing fast.
Much more needs to be done to secure America’s elections, and important new safeguards could be put in place by 2018. States still using paperless voting machines should replace them with optical scan systems, and all states should update their audit and recount procedures. There are fast and inexpensive ways to verify (or correct) computer voting results using a risk-limiting audit, a statistical method that involves manually inspecting randomly selected paper ballots. Officials need to begin preparing soon to make sure all of these improvements are ready before the next big election.
J. Alex Halderman is Professor of Computer Science & Engineering at the University of Michigan and Director of Michigan’s Center for Computer Security & Society. His course on election technology, Securing Digital Democracy, is available on Coursera. He was recently named by Popular Science as one of the “ten brightest minds reshaping science, engineering, and the world.”





 Microsofts nieuwe Surface Studio-pc. © Microsoft.
Microsofts nieuwe Surface Studio-pc. © Microsoft. © Microsoft.
© Microsoft.